System Files: 7 Essential Facts You Must Know Now
Ever wondered what keeps your computer running smoothly behind the scenes? It’s not magic—it’s system files. These hidden but vital components power everything from startup to shutdown, silently managing your device’s core functions every second.
What Are System Files and Why They Matter

At the heart of every operating system lies a collection of critical components known as system files. These are not ordinary files you create or download; they are pre-installed, protected, and essential for the proper functioning of your computer. Without them, your operating system would fail to boot, applications wouldn’t launch, and hardware wouldn’t communicate properly.
Definition and Core Function
System files are specialized files that form the backbone of an operating system. They include executable binaries, configuration files, drivers, libraries, and boot loaders. These files are responsible for managing hardware resources, launching services, and ensuring smooth communication between software and hardware layers.
- They enable the OS kernel to interact with physical components.
- They store settings and preferences critical to system stability.
- They support essential processes like memory management and file system access.
For example, in Windows, files like ntoskrnl.exe (the Windows kernel) or hal.dll (Hardware Abstraction Layer) are indispensable. On Linux, files such as vmlinuz (compressed kernel image) and configuration files in /etc serve similar roles. You can learn more about core system components at The Linux Kernel Archives.
Difference Between System Files and User Files
Understanding the distinction between system files and user files is crucial for maintaining system integrity. User files are documents, photos, videos, or downloads created or saved by the user. In contrast, system files are owned and managed by the operating system itself.
- User files can be freely modified, moved, or deleted without affecting system operation.
- System files are typically locked, hidden, and protected by permissions to prevent accidental or malicious changes.
- Modifying or deleting system files often requires administrative privileges.
“System files are like the DNA of your computer—alter them carelessly, and the entire organism may fail.”
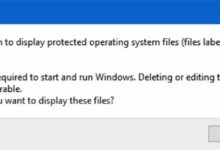
Operating systems use access control lists (ACLs) and file attributes (like the ‘hidden’ or ‘read-only’ flags) to safeguard these files. For instance, in Windows, the TrustedInstaller service owns many critical system files, preventing even administrators from modifying them without explicit permission changes.
Types of System Files in Modern Operating Systems
Different operating systems organize and utilize system files in unique ways, but they all share common categories based on function. Whether you’re using Windows, macOS, or Linux, understanding these types helps in troubleshooting, optimization, and security management.
Executable and Kernel Files
Executable system files contain machine code that the CPU runs directly. The most important of these is the kernel—the central module of the OS that manages system memory, processes, and hardware communication.
- In Windows,
ntoskrnl.exeis the main kernel file located inC:WindowsSystem32. - On Linux, the kernel is usually named
vmlinuzand stored in/boot. - macOS uses a hybrid kernel called XNU, with components stored in
/mach_kernel(legacy) or within the System Volume.
These files are loaded into memory during boot and remain active throughout the session. Tampering with them can lead to boot failures or Blue Screens of Death (BSOD) in Windows. More technical details about kernel architecture can be found at Wikipedia’s Kernel Page.
Configuration and Registry Files
Configuration files store settings that dictate how the OS and its services behave. These can be plain text files, binary databases, or structured data formats like XML or JSON.
- Windows uses the Windows Registry—a hierarchical database stored in files like
SYSTEM,SOFTWARE, andSECURITYinC:WindowsSystem32config. - Linux relies heavily on text-based config files in directories like
/etc, such as/etc/fstabfor disk mounting or/etc/passwdfor user accounts. - macOS combines both approaches, using
.plist(property list) files in/Library/Preferencesand~/Library/Preferences.
These files control everything from network settings to startup programs. A misconfigured file can disable internet access or prevent login. Always back up configuration files before editing them.
Device Drivers and Dynamic Link Libraries
Device drivers are system files that allow the OS to communicate with hardware peripherals like printers, graphics cards, and network adapters. They act as translators between high-level OS commands and low-level hardware instructions.
- Drivers are often packaged as
.sysfiles in Windows or kernel modules (.ko) in Linux. - Dynamic Link Libraries (DLLs) in Windows (
.dllfiles) provide shared code that multiple programs can use simultaneously, reducing redundancy. - Linux uses shared object files (
.so) for similar purposes.
For example, dxgkrnl.sys is the DirectX graphics kernel in Windows, crucial for gaming and display performance. If corrupted, it can cause display glitches or crashes. You can explore official driver resources at Intel Driver & Support Assistant.
How System Files Work During Boot Process
The boot process is one of the most critical phases where system files play a decisive role. From the moment you press the power button to when the desktop appears, dozens of system files are loaded in a precise sequence to initialize the system.
BIOS/UEFI and Bootloader Interaction
The journey begins with the firmware—either BIOS (Basic Input/Output System) or its modern successor, UEFI (Unified Extensible Firmware Interface). This low-level software performs a Power-On Self-Test (POST) and locates the bootloader.
- The bootloader (e.g.,
bootmgrin Windows,GRUBin Linux) is a small system file responsible for loading the OS kernel. - It reads configuration data from files like
BCD(Boot Configuration Data) in Windows orgrub.cfgin Linux. - If these files are missing or corrupted, the system may display errors like ‘No operating system found’.
UEFI firmware enhances security by supporting Secure Boot, which verifies the digital signature of bootloader files to prevent malware injection. This is a key defense against rootkits that target early boot stages.
Loading the Kernel and Initialization
Once the bootloader locates the kernel, it loads it into RAM. The kernel then initializes core subsystems such as memory management, process scheduling, and device drivers.
- In Linux, the initramfs (initial RAM filesystem) is a temporary root file system loaded into memory to assist in mounting the real root filesystem.
- Windows uses the Windows Boot Manager and loads
ntoskrnl.exe, followed by essential services via the Service Control Manager (SCM). - The kernel reads hardware information from ACPI tables and configures devices accordingly.
This phase is highly dependent on the integrity of system files. A single corrupted file can halt the boot process. Tools like Windows Recovery Environment (WinRE) or Linux Live CDs can help repair these files.
User Session and Service Activation
After the kernel is up, the system transitions to user space. This involves launching system services and preparing the login interface.
- Windows starts services defined in the registry under
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServices. - Linux uses
systemdorinitto start daemons based on configuration in/etc/systemd/systemor/etc/init.d. - macOS uses
launchdto manage system-wide and per-user services.
These services include networking, audio, printing, and security agents. They rely on associated system files for configuration and execution. Any failure here may result in a functional OS that lacks key features.
Common Issues Caused by Corrupted System Files
Despite their protection, system files can become corrupted due to malware, power outages, disk errors, or failed updates. When this happens, the consequences can range from minor glitches to complete system failure.
Boot Failures and Startup Errors
One of the most severe issues is the inability to boot. This often stems from missing or damaged bootloader or kernel files.
- Error messages like ‘BOOTMGR is missing’ or ‘Invalid partition table’ indicate bootloader problems.
- ‘INACCESSIBLE_BOOT_DEVICE’ in Windows usually points to a corrupted driver or disk configuration file.
- Linux users may see ‘Kernel panic – not syncing’ due to a faulty kernel image or missing initramfs.
These errors prevent the OS from loading, leaving the user stranded at a black screen or recovery prompt. Recovery typically requires external media and repair tools.
Application Crashes and Performance Degradation
Corrupted DLLs or shared libraries can cause applications to crash unexpectedly. For example, a damaged msvcrt.dll in Windows can break multiple programs that depend on it.
- Users may experience frequent freezes, error dialogs, or programs failing to launch.
- Performance may degrade due to inefficient system calls or memory leaks caused by faulty drivers.
- Some malware disguises itself as legitimate system files (e.g.,
svchost.exein the wrong directory) to evade detection.
Running system file checks (like SFC in Windows) can often resolve these issues by restoring original versions from a cached backup.
Blue Screen of Death and Kernel Panics
The Blue Screen of Death (BSOD) in Windows and kernel panics in Linux/macOS are last-resort error screens triggered when the OS encounters a critical failure it cannot recover from.
- Common causes include faulty drivers, memory corruption, or incompatible system files.
- Error codes like
IRQL_NOT_LESS_OR_EQUALorKMODE_EXCEPTION_NOT_HANDLEDoften point to driver or kernel file issues. - Crash dumps (memory.dmp files) can be analyzed to identify the problematic file.
“A BSOD is the OS screaming for help—its last message before collapsing.”
Tools like Windows Debugger (WinDbg) or Linux crash utility can parse these dumps to pinpoint the offending system file.
How to Protect and Repair System Files
Given their critical nature, protecting system files from corruption and knowing how to repair them is essential for system stability and security.
Using Built-in Repair Tools (SFC, DISM, fsck)
Modern operating systems come with built-in utilities designed to scan and repair system files.
- Windows offers System File Checker (SFC): Run
sfc /scannowin Command Prompt to detect and replace corrupted files using a cached copy from%WinDir%System32dllcache. - DISM (Deployment Image Servicing and Management) goes deeper, repairing the Windows image itself with commands like
DISM /Online /Cleanup-Image /RestoreHealth. - Linux uses
fsck(file system check) to repair filesystem metadata, and package managers likeaptordnfcan reinstall corrupted system packages.
These tools are your first line of defense. For more information on SFC, visit Microsoft Support.
Enabling System Restore and File Protection
Windows includes System Protection, which creates restore points—snapshots of system files and settings at specific times.
- If a recent change (like a bad driver update) breaks the system, you can roll back to a working state.
- Windows File Protection (WFP) automatically prevents unauthorized replacement of critical system files.
- macOS Time Machine and Linux snapshots (via Btrfs or LVM) offer similar rollback capabilities.
Ensure System Restore is enabled on your main drive. It uses minimal space but can save hours of troubleshooting.
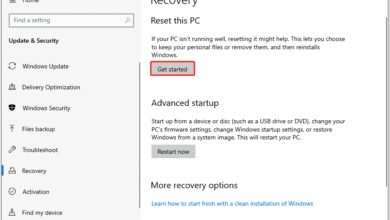
Manual Recovery Using Installation Media
When automated tools fail, manual recovery using installation media (USB/DVD) becomes necessary.
- Boot from the media and select ‘Repair your computer’ (Windows) or ‘Rescue mode’ (Linux).
- Replace corrupted files manually from the installation source.
- Rebuild the bootloader using tools like
bootrec /fixmbrandbootrec /rebuildbcdin Windows.
This method requires technical knowledge but is often the only solution for severe corruption.
Security Risks Associated with System Files
Because system files have high privileges and deep access to the OS, they are prime targets for attackers. Malware often attempts to modify or impersonate them to gain persistence and evade detection.
Malware Disguised as System Files
Cybercriminals frequently name malicious files after legitimate system files to blend in.
- A file named
csrss.exeinC:Usersinstead ofC:WindowsSystem32is almost certainly malware (the real csrss.exe should only be in System32). - Tools like Task Manager or Process Explorer can show the file location and digital signature to verify legitimacy.
- Antivirus software uses heuristic analysis and cloud databases to flag suspicious imposters.
Always verify the file path and signature. Legitimate Microsoft files are digitally signed and located in protected directories.
Rootkits and Kernel-Level Infections
Rootkits are among the most dangerous threats because they operate at the kernel level, often by replacing or patching system files.
- They can hide processes, files, and network connections from the OS itself.
- Kernel-mode rootkits modify
ntoskrnl.exeor load malicious drivers signed with stolen certificates. - Detection requires specialized tools like Microsoft’s Sysinternals Suite or GMER.
Prevention includes enabling Secure Boot, keeping systems updated, and avoiding untrusted software.
Unauthorized Modifications and Privilege Escalation
Attackers who gain administrative access may modify system files to create backdoors or disable security software.
- Changing
hostsfile to redirect domains to phishing sites. - Replacing
lsass.exeto capture login credentials (as in Mimikatz attacks). - Disabling Windows Defender via registry edits.
Implementing least-privilege policies and using integrity monitoring tools can help detect such changes.
Best Practices for Managing System Files
Proper management of system files ensures system reliability, performance, and security. While most users should avoid direct interaction, understanding best practices is invaluable.
Never Modify System Files Without Backup
If you must edit a system file (e.g., for debugging or configuration), always create a backup first.
- Copy the original file to a safe location with a timestamp.
- Use system restore points before making changes.
- Document the reason for the change to aid future troubleshooting.
For example, before editing hosts file to block ads, duplicate it as hosts.bak. If something goes wrong, you can revert instantly.
Keep Your OS and Drivers Updated
Regular updates are the best way to maintain system file integrity.
- Updates often include patches for known vulnerabilities in system files.
- Driver updates fix bugs and improve compatibility with new hardware.
- Enable automatic updates where possible to stay protected.
Microsoft, Apple, and Linux distributions regularly release security updates. Ignoring them increases exposure to exploits targeting outdated system components.
Use Trusted Tools and Avoid Third-Party ‘Optimizers’
Many third-party ‘PC cleaner’ or ‘registry optimizer’ tools claim to improve performance by tweaking system files—but they often do more harm than good.
- They may delete or modify critical files based on flawed logic.
- Some bundle adware or spyware.
- They bypass built-in protections, increasing the risk of instability.
Stick to official tools from Microsoft, Apple, or your Linux distribution. For diagnostics, use trusted utilities like Sysinternals, top, or htop.
What are system files?
System files are essential components of an operating system that manage core functions like booting, hardware communication, and system services. They include executables, drivers, configuration files, and libraries necessary for the OS to operate.
Can I delete system files to free up space?
No, you should never manually delete system files. Doing so can cause system instability, boot failures, or security vulnerabilities. If you need to free space, use built-in tools like Disk Cleanup or remove user files instead.
How do I fix corrupted system files in Windows?
Use the System File Checker (SFC) tool by running ‘sfc /scannow’ in an elevated Command Prompt. If that fails, run DISM to repair the Windows image. For persistent issues, use installation media for manual repair.
Are system files the same across different operating systems?
No, system files vary significantly between operating systems. Windows uses .dll and .sys files, Linux uses .ko and text-based configs, and macOS uses .kext and .plist files. Each OS has a unique architecture and file organization.
Can malware infect system files?
Yes, malware can infect or replace system files to gain persistence and elevated privileges. This is especially dangerous with rootkits that operate at the kernel level. Use antivirus software and enable Secure Boot to reduce this risk.
System files are the invisible foundation of your computer’s operation. From enabling the boot process to managing hardware and running applications, they perform countless critical tasks behind the scenes. While they’re protected by design, they’re not immune to corruption or attack. Understanding what they are, how they work, and how to protect them empowers you to maintain a stable, secure, and efficient system. Whether you’re troubleshooting a BSOD or simply curious about what happens at startup, respecting the role of system files is key to mastering your device.
Recommended for you 👇
Further Reading: